34 LONG condition between TD and ASD. Top figure illustrates the t/f... | Download Scientific Diagram

Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo. - ppt video online download
PLOS ONE: Association between the Infant and Child Feeding Index (ICFI) and nutritional status of 6- to 35-month-old children in rural western China

ASSR power analysis. Top panels (a, b): ASSR beamformer localization.... | Download Scientific Diagram

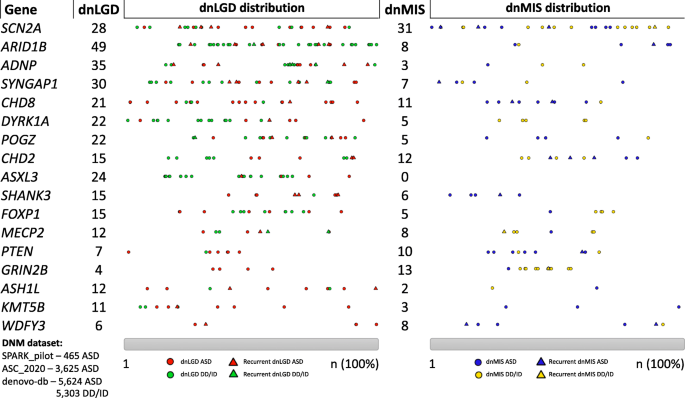
Large-Scale Exome Sequencing Study Implicates Both Developmental and Functional Changes in the Neurobiology of Autism - ScienceDirect

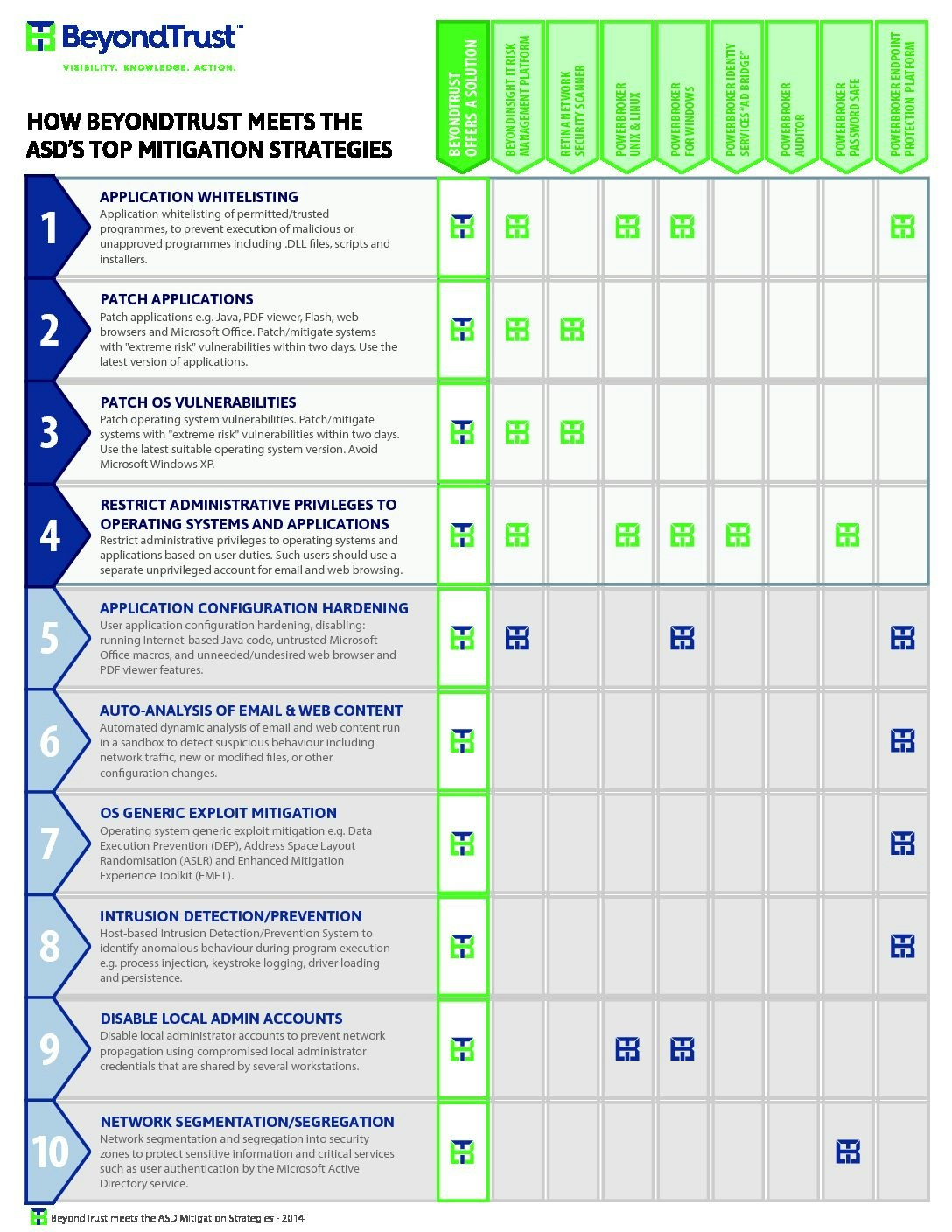
Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download

Buy ASD 2x4 LED Drop Ceiling Light with Motion Sensor 35-50W Power Adjustable, 4CCT Color Adjustable 3000K-5000K, 120-277V, Dimmable 0-10V, Lay in Flat Back-lit Fixture, UL, DLC Premium, 2 Pack Online in

Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo. - ppt video online download
Reflections on the genetics-first approach to advancements in molecular genetic and neurobiological research on neurodevelopmental disorders | Journal of Neurodevelopmental Disorders | Full Text

Buy ASD 2x4Ft LED Edge Lit Panel Light Color Temperature Selectable 3000-5000K, Power Adjustable 35-50W with Motion Sensor - 5250 Lm, 120-277V Indoor Commercial Fixture, UL & DLC, 2 Pack Online in Poland. B08VDNSFC7

Important features for classification are different across sub-groups.... | Download Scientific Diagram
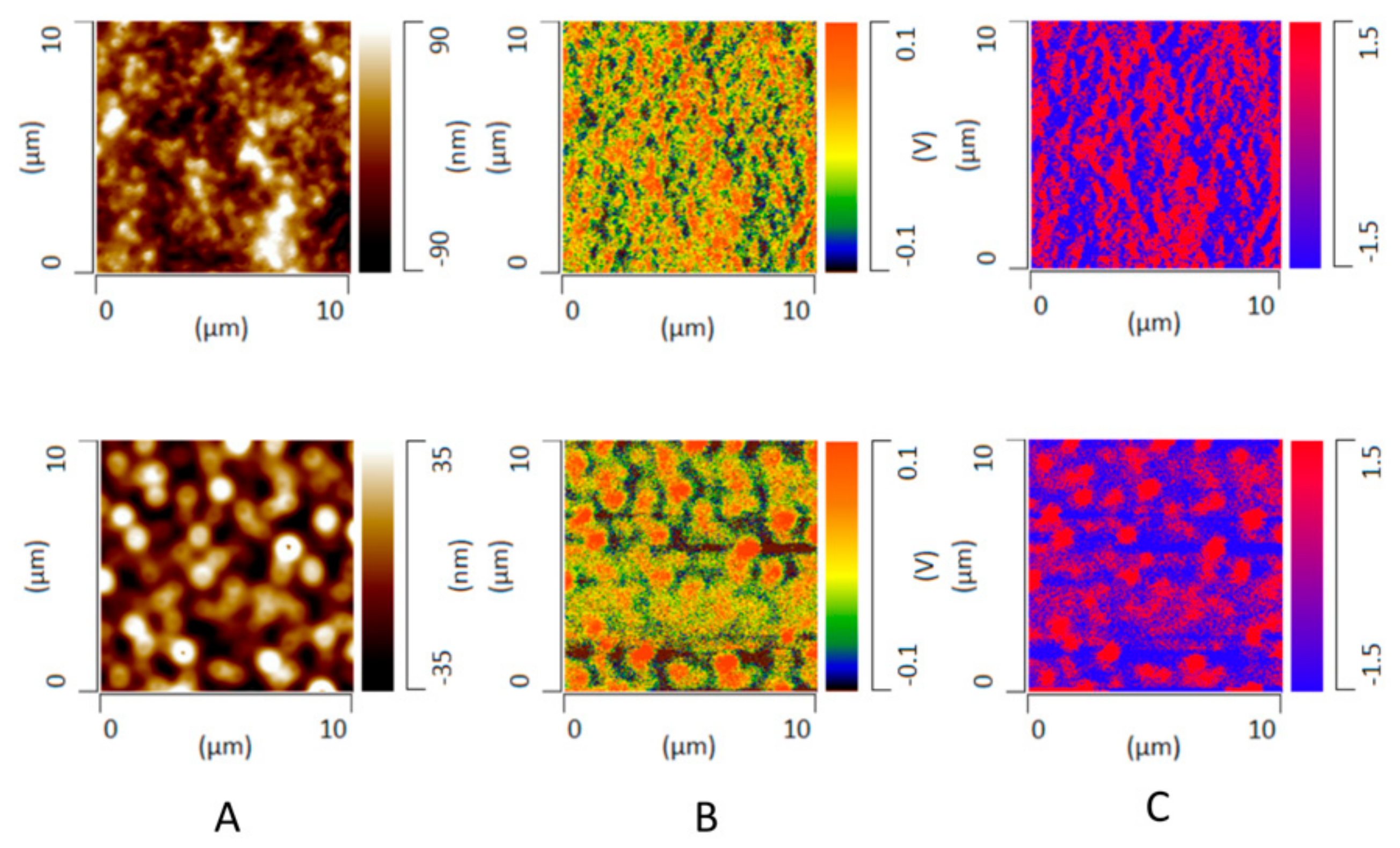
Pharmaceutics | Free Full-Text | Exploring the Role of Surfactants in Enhancing Drug Release from Amorphous Solid Dispersions at Higher Drug Loadings | HTML








![Protecting Your Data Wherever it Goes [Infographic] - Verizon Small Business Essentials Resources Protecting Your Data Wherever it Goes [Infographic] - Verizon Small Business Essentials Resources](https://s2.yimg.com/lm/ysbp/img/8HSAw3_UtdkoHw_IJ6HcLIwymps_l5jp0fq3kbQsTqTeLdr2tvPbM5SEhADGE2wj.jpg)